Third Party Risk Management
The December 8th Telarus Tuesday call welcomed RSI VP of sales & marketing, Trish Kapos, and director of assessment services, Angela Hogaboom, to discuss why you should be outsourcing third party risk management to RSI. The entire recording is available here.
The Problem
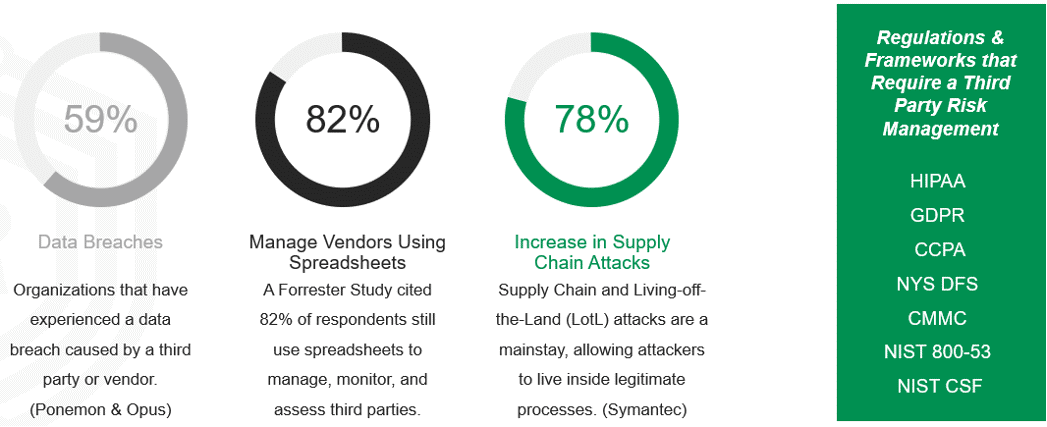
Fifty-nine percent of respondents to a Ponemon & Opus study stated that they had experienced a data breach caused by a third party or vendor. Most major breaches covered by the media have third party roots; think Target, Home Depot, General Electric, and Instagram. Despite the commonality of third-party breaches in the news, only forty-four percent of businesses report on risk to their executives or boards regularly, and eighty-two percent manage vendor information, monitoring, and assessments using spreadsheets or manual processes. These statistics demonstrate the ease in which attackers can access information without penetrating individual businesses. On the supply chain side, there has been a seventy-eight percent increase in attacks, including living off the land attacks.
What is a Third Party?
So, what is Third-party Risk Management (TPRM)? It is the practice of identifying, assessing, and controlling risks presented throughout the lifecycle of your relationship with third parties. When we think of third parties, we commonly associate the term “vendor.” While a vendor is a third party, there are others to consider when we talk about the third-party risk landscape. Third parties can be any of the following:

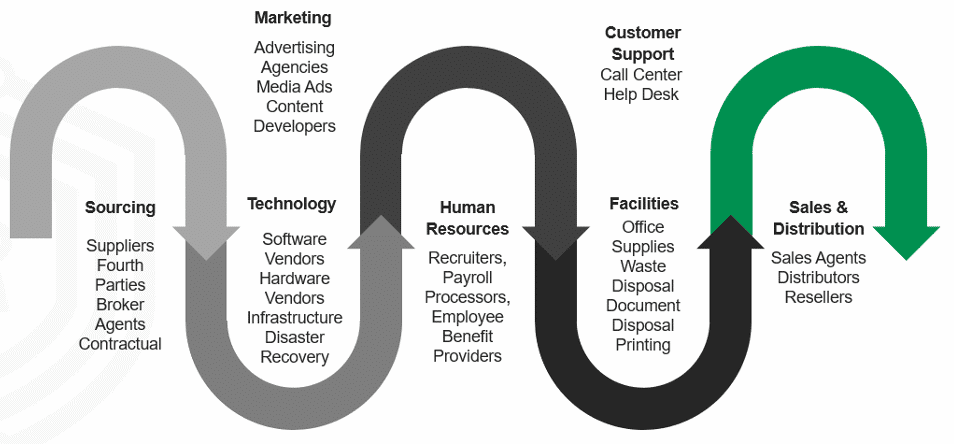
This third-party ecosystem expands across the enterprise, providing critical functions and services within each department. Third parties have varying access to information. Third parties, like cleaning services, have access to secured areas and equipment. Others have access and process data on behalf of the business, and some, like contractors, may have access to intellectual property and trade secrets. This means that there is no third party that is risk-free. To provide a little context on the impact of third parties organizations:
Managing third-party risk across an organization presents numerous challenges. Manual processes can be time-consuming, and in companies that don’t have dedicated personnel, the job is often assigned as a secondary role. In larger companies, the person or people responsible for managing risk spend dozens of hours using manual processes that don’t always identify gaps or have a verified monitoring method. Network complexity presents challenges related to the expanding third-party ecosystem. Issues like applications sprawl or Shadow IT can lead to unexpected risk and unexpected bills. Lack of governance, policies, and procedures that address third-party risk is another challenge because organizations without a compliance department lack the awareness necessary to build an effective program. Perhaps the biggest challenge in addressing third-party risk is prioritizing and classifying vendors and monitoring them in a way that is effective and useful. Leaders in the risk management and cybersecurity industry are aware of these challenges and are creating platforms that simplify the third-party risk process.

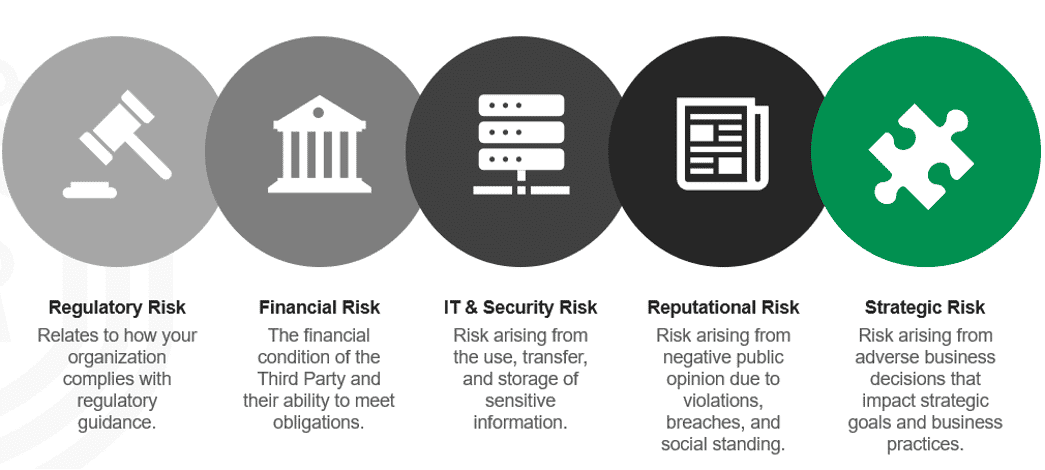
Cyber risk isn’t the only risk posed by a third party. There is also a regulatory risk, financial risk, IT and security risk, reputational risk, and strategic risk.
The RSI Approach
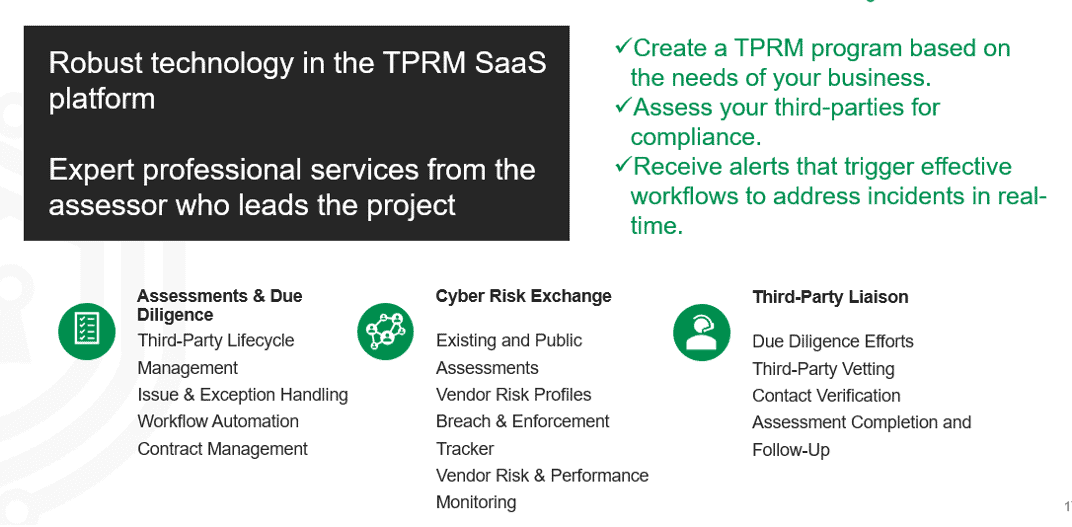
RSI is here to provide help when it comes to Third-Party Risk Management, this is their approach:
Below we have listed a few qualifying questions you can ask your potential customers:
- How are you managing third parties for security and compliance?
- If you lost a particular vendor, would your business continue?
- Do you monitor your critical vendors for data breaches?
- Do you run credit reports on your vendors?
- What is your contingency for vendors who experience an outage?
To learn more about RSI visit, https://www.rsitex.com.